Mobile app that uses phone sensors and third-party APIs to automate the filling of a document required to pass the belgian driving license. It uses ReactNative and Firebase Authentication, Functions, Firestore, Storage and Cloud Security rules.
2023
In a team of 4 people, we participated twice to the Cyber Security Challenge Belgium. We made it to the last day of the finals at the Royal Military Academy in 2023 and reached 10th place out of 290 in 2024. We solved many CTF challenges as well as various challenges from industry experts.
Mar. 2023 & Mar. 2024
In a team of 5 we participated in a 15 hours-long Capture the Flag and ranked 8th place on 25 teams.
Oct. 2023
Workshop on mobile games hacking doing dynamic and static analysis on Android Studio debugger and modifying compiled APKs using Ghidra.
Apr. 2023
My team mate and I reached 5th place in the first edition of this algorithmic contest. We had to solve as many problems as possible with the right time complexity having a single computer and no internet access except Python documentation.
Apr. 2023
24 days of red, blue or purple cyber security challenges every day until Christmas.
Dec. 2022
One week to work on open-source projects, my team worked on implementing MPTCP protocol into OpenSSH
Jun. 2022

24 hours to build an open-source video game in Python in teams of 4 people.
Mar. 2021
Android App to manage cooking recipes, written in Kotlin and using Android’s Room Database.
Apr. 2021The source codes of the projects are stored on private GitHub repositories.
Please do not hesitate to ask me to grant you access to these.

Modelling and solving instances of a logistics and transportation problem using Constraint Programming.
Second term 2024
Highly maintainable and evolvable Java context-aware application, exploiting design patterns and Object Oriented techniques.
First term 2024
Automated program to find ways of crashing an executable by trying lots of valid, invalid and border case inputs.
Second term 2023
Creation of a whole compiler for a fictive programming language, from lexing the text tokens to generating the executable Java byte code.
Second term 2023
Network attacks implemented in Python for a Mininet composed of workstations, servers, switches, routers and internet access and their corresponding Firewall rules to prevent them.
Second term 2023
Predict as best as possible the binary classes from a raw dirty dataset, from real industry data, composed of many csv files with a lot of features but only a few examples. We were free to use any machine learning techniques.
Second term 2023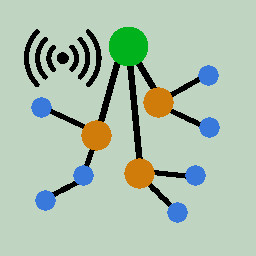
Implementing routing and scheduling protocols running on top of IEEE 802.15.4 in a multihop network composed of many wireless devices scattered across several areas of a fictive building. Enabling a reliable wireless transfer from the sensors up to the external server in the tree shape.
Second term 2023
Mini-internet network built using FRRouting and Open vSwitch. Configured the hosts, switches and routers with OSPF, BGP and routing policies between ASes.
First term 2023
Micro-services e-commerce application able to elastically scale up and down to handle the load. Built using Node.Js, React and CouchDB with services running as Docker containers hosted on Azure VMs.
First term 2023
Optimization of a multithreaded client-server in C, doing line-by-line matrix multiplication with AVX vector instructions, loop unrolling and aligned memory allocation.
First term 2023
Comparison of ISP latencies and throughputs in European countries from data available on Ripe Atlas and M-Lab.
First term 2023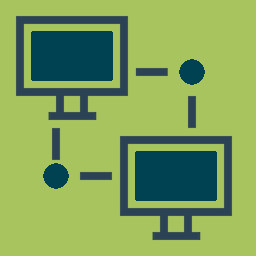
Truncated reliable transport protocol based on UDP, using Selective Repeat and FEC packets to handle loss, corruption, duplication, delay and latency.
Second term 2022
Built an Android mobile application in Java, using Firebase Authentication and Firestore.
Second term 2022
Analyzing graphs of bitcoin transactions in python to get values such as page rank, balance degree, triadic closures, path lengths, bridges, etc.
Second term 2022
Doing data exploration, feature selection/extraction, modelling and cross-validation on a big dataset.
Second term 2022

Customized version of Captain Sonar in turn by turn or simultaneous using only declarative code and multi-agent programming.
First term 2022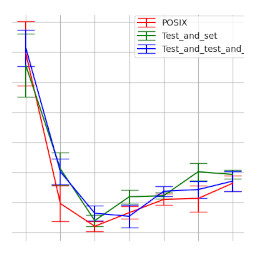
Comparing the performance of the POSIX library with our own test-and-test-and-set on Reader-Writer, Consumer-Producer and Philosopher diner problem.
First term 2022
Program in C to handle tar archives (analyze the structure, list the files in a folder, follow symbolic links, etc.).
First term 2022
Multithreaded C program to compute clusters and centroids from graphs stored as binary files.
Second term 2021
“Guess Who?” style game created using Oz language (no loops and single assignment).
Second term 2021

Web App to manage groups of people with todolist, planning and expenses manager. Built with JavaScript, Node.js, Express, bcrypt, Bootstrap, HTML and CSS.
First term 2021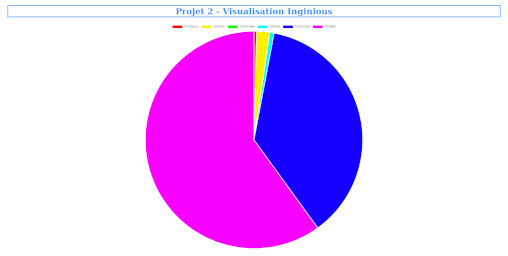
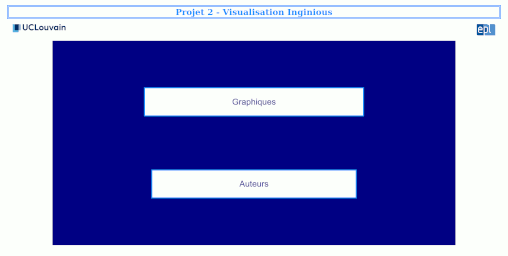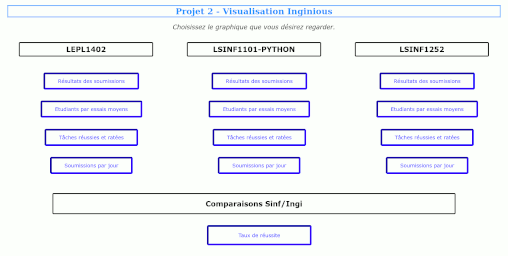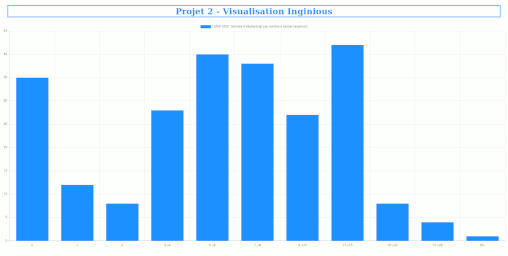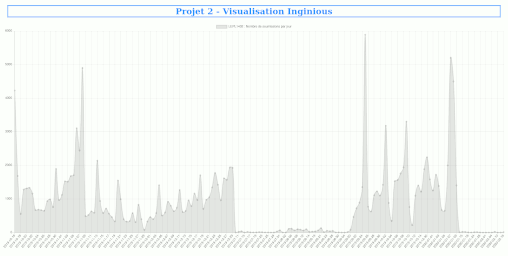
Website for visualizing graphs using Flask, Chart.js, HTML and CSS.
Second term 2020
Python program to encrypt and decrypt messages using the sensors from a Raspberry Pi Sense Hat.
First term 2020
Graduated with The Greatest Distinction
Major in Security and Networking
Major in Artificial Intelligence
Thesis: Energy-Aware Scheduling for ISA-Heterogeneous Clusters
2022 - 2024
Graduated with Great Distinction
Minor in Additional module in computer science
2019 - 2022
Amazon Web Services Training and Certification
AWS Nov. 2024 see credentials
Amazon Web Services Training and Certification
AWS Sept. 2024 see credentials




